Embedded Trust In Your Software
Karambit.AI streamlines product release, compliance, and software updates by performing static analysis to detect and verify the integrity of software safety, cybersecurity, and functionality behaviors prior to deployment without source code.
Our Process
With our Software Bill of Behaviors
Unmask any known unknowns, intended and unintended change, while bringing transparency, visibility and control to your software supply chain.
Our Focus
We empower organizations to deeply understand the behavior of their software components.
.png)
Comparative Analysis
Analysis of software updates over time provides context for what behaviors are normal or abnormal for a given application.
.png)
Flag Malicious Code Injections
Detect attacks in end-user software by highlighting anomalous behavioral intents and clearly identify the added capabilities.
1.
Eliminate Remediation Costs
Find hidden malicious behaviors before deployment, stopping problems before they cost time, money, and reputation damage
2.
Scale
Quick and automatically identify hidden and unintended behaviors, reducing time to update software and maintain compliance
3.
Validate Trust
Mitigate risks other tools would miss and get a better understanding of the behavioral profile of the software you intend to deploy.
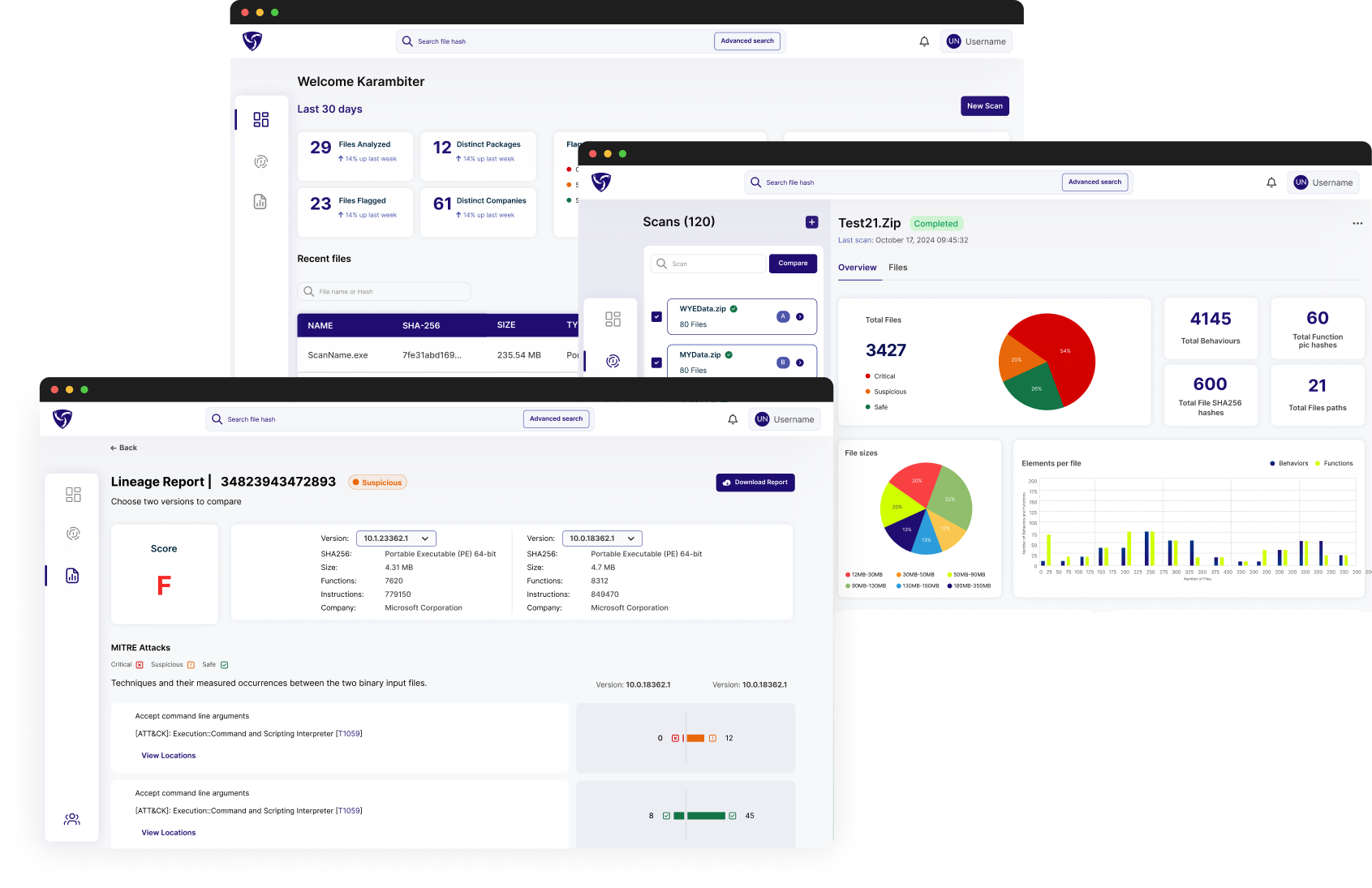

Karambit’s use of a contents historical functionality and changes, set itself apart from traditional static analysis.
With this innovative perspective, we are looking forward to insight into content that we have not had previously.
Securing the supply chain is very important to protect Microsoft’s customers and brand.
Mike Bush
Product Manager at Microsoft

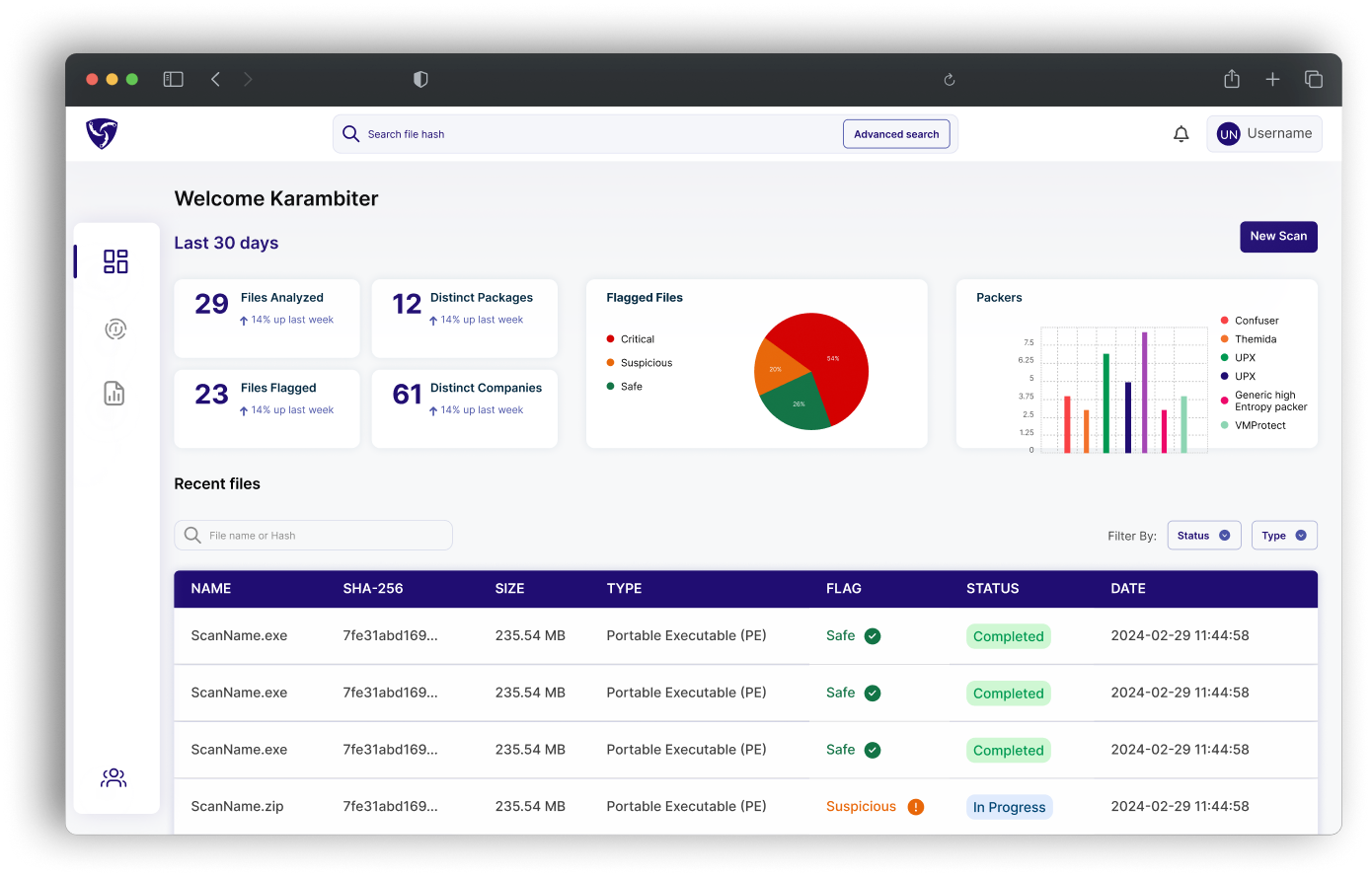
.png)


